AUTHOR: Arne Klopper As organisations move into the cloud, a risk – if not addressed early on, is the correct access control implementation across the Azure landscape. From initial Proof of concepts to testing in the cloud, sometimes the Role-based Access Control model utilised when starting…
Azure vs Azure AD Security
It is important to understand that there are two key implementations of your Azure estate when it gets to assigning permissions. This is the distinction between Azure AD and Azure. The Microsoft diagram below illustrates the difference the best.
All users live inside Azure AD, however they have different roles in Azure AD and in the Azure Account (infrastructure).
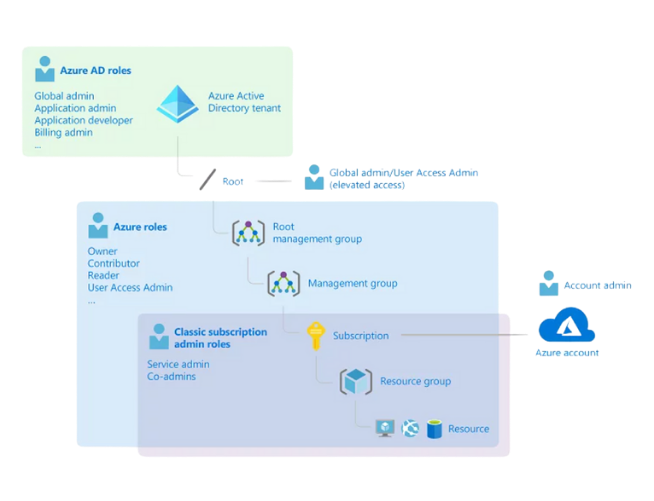
Azure AD
There is a lot of Azure Active Directory (Azure AD) built-in roles, which are roles with a fixed set of role permissions. To supplement the built-in roles, Azure AD also supports custom roles. Use custom roles to select the role permissions that you require, try avoid too…
Azure RBAC
As your cloud estate grows it is recommended to keep your management of the access controls relatively simple to avoid more difficult management due to complexity. The Top 3 Tips to make your Access Control easier in Azure are: Use management groups for organisation-wide…
Management Group Organisation
As part of Microsofts’ Cloud Adoption Framework, a guide for management group and subscription organization, you are provided with a set of hierarchy design recommendations and considerations for management groups and subscriptions.
Using Privilege Identity Management (PIM)
Microsoft has several offerings to support identity management in Azure including Azure Active Directory (AAD), Azure Active Directory Identity Protection and Azure AD Privileged Identity Management (PIM). PIM provides time-based and approval-based role activation to mitigate the risks of excessive, unnecessary, or misused access permissions in your Azure estate.…
LESSONS LEARNED
Working with our customers we’ve seen how the lack of governance can result in a large administrative burden for support teams and complexity which is hard to unstitch. This results in unmanaged risk and long change control cycles to remediate the deployment to a governed approach. PIM is…



